Ever since virtual and hosted desktops emerged, connection brokers have been used to securely connect end-users to resources hosted in the data center. But what’s really going on behind the scenes? In this blog we pull back the curtain to give you some insight into how a connection broker manages users.
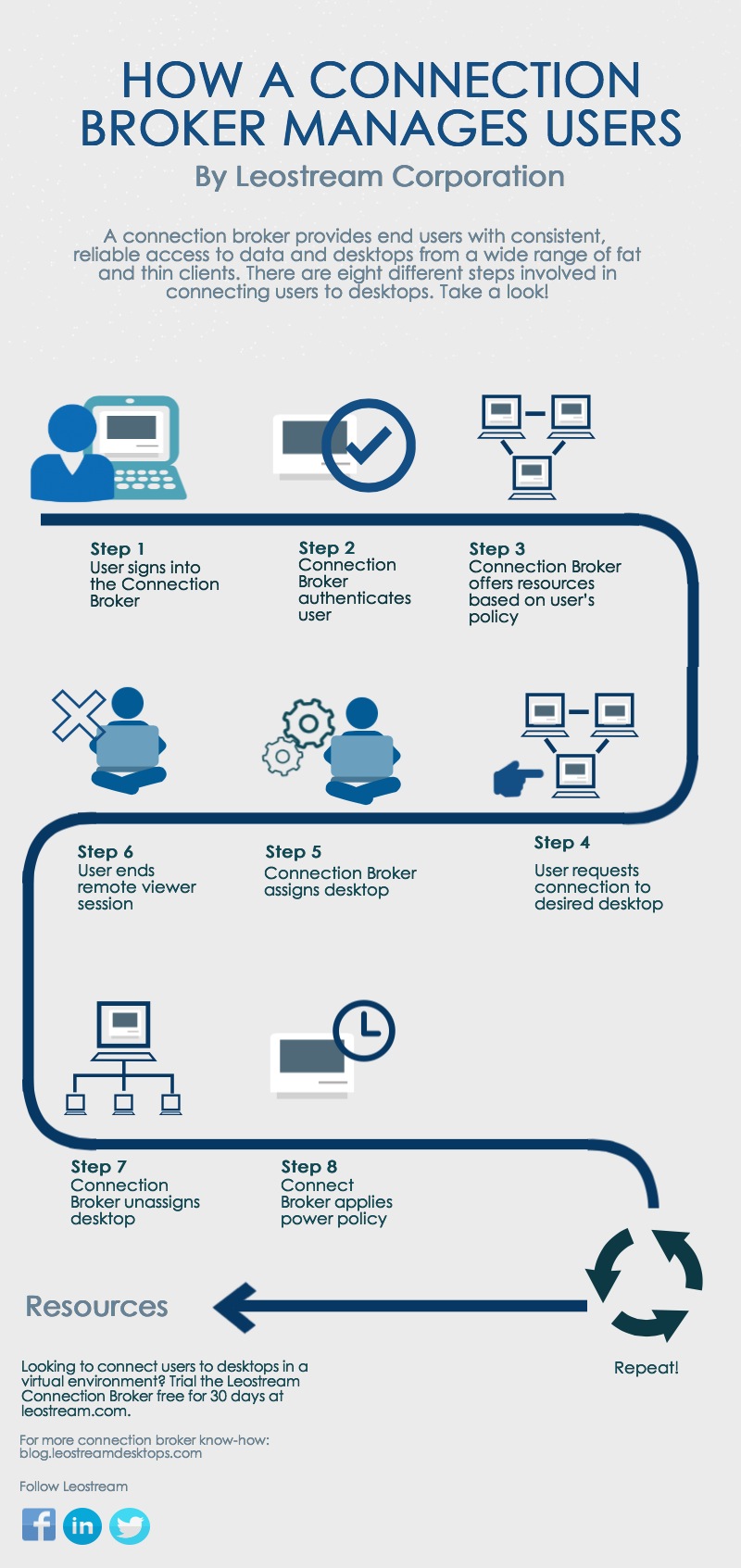
Let’s dig a little deeper. Using Leostream’s Connection Broker as an example, here’s how each step is handled.
1. User signs into the Connection Broker: End users can log into the Connection Broker from a Web browser, thin client, mobile device, or Leostream Connect. Different clients support different types of credentials, such as user name/password, smart cards, or fingerprints.
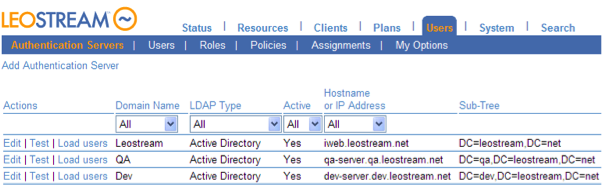
2. Connection Broker authenticates user: Once the Connection Broker has the user’s credentials, it searches for the user in the domains defined in the > Users > Authentication Servers page. If the user previously logged in, the Connection Broker begins by looking in the authentication server used for that login then searches the remaining authentication servers in the order defined by the authentication server’s Position. If this is the first time the user logged in, the Connection Broker searches all authentication servers in order of their position.
3. Connection Broker offers resources based on user’s policy: The Connection Broker then assigns a policy using the assignment table associated with the authentication server chosen in step 2. The policy determines the desktops and applications offered to the user, the VMware View Connection Servers this user can log in to, the USB passthrough permissions, and the display protocol to use.
4. User requests connection to desired desktop: If the user is assigned multiple resources, they must select the desktops and applications to launch.
5. Connection Broker assigns desktop: After the user selects one or more resource, the Connection Broker assigns those resources to the user. Once a resource is assigned to a user, the Connection Broker will not offer that resource to another user. After the assignment is made, the Connection Broker initiates the remote viewer session.
6. User ends remote viewer session: When the user disconnects or logs out of the remote viewer session, the Connection Broker applies any power control or release actions specified by the plans assigned to that desktop in the user’s policy.
7. Connection Broker unassigns desktop: If the user’s policy releases the desktop back to its pool, the Connection Broker unassigns the desktop. Otherwise, the Connection Broker retains the desktop assignment.
8. Connect Broker applies power policy: Lastly, the Connection Broker takes any power control actions set in the user’s policy.
